Data Security that Starts with Identity™
Netwrix is reinventing data security because traditional solutions fail if adversaries can exploit identities and escalate privileges.
Netwrix starts by protecting identity, the #1 attack vector, and in parallel, classifies data, identifies risks, removes exposures, controls privilege, enforces data loss prevention (DLP) policies, blocks threats, and streamlines recovery to secure each organization’s most valuable asset, their data.
Trusted by 13,500+ organizations
Our Solutions:
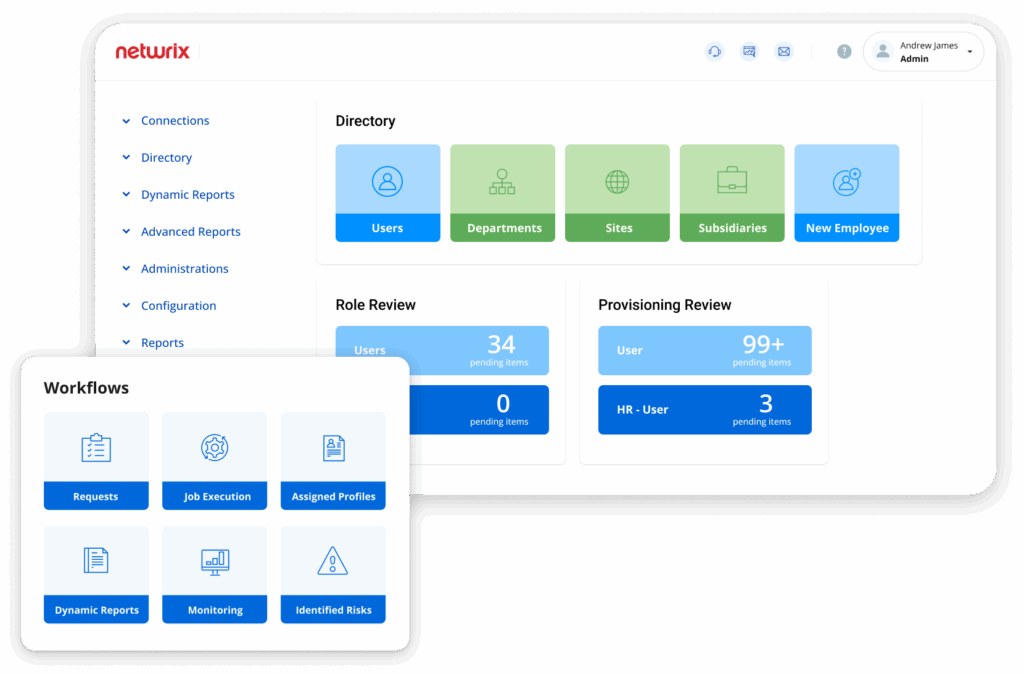
Netwrix Identity Management strengthens security, automates compliance, and streamlines user access management. It supports zero-trust governance, automates group and user lifecycle management, enforces strong password policies to reduce credential risks, and minimizes administrative overhead while ensuring timely, appropriate access.
- Identity Lifecycle and Workflows
- Password Policy Enforcement
- Access Rights Certification
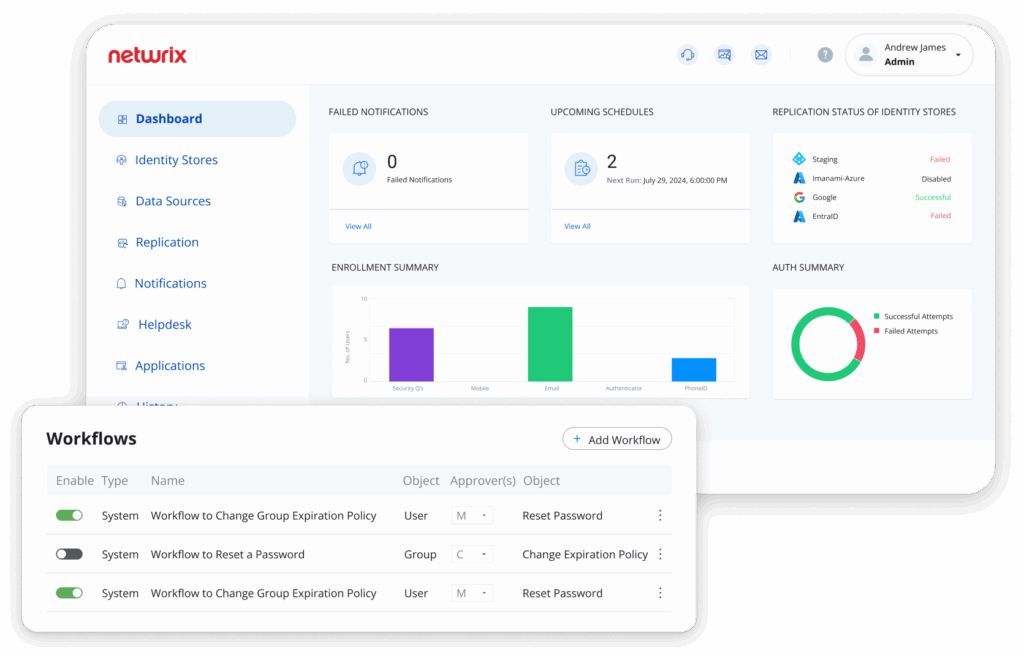
Netwrix Directory Management enhances security and compliance with detailed auditing of on- premises and cloud directories, ensuring visibility into changes and access events. It streamlines user and group management through automation and delegation and enforces customizable password policies to reduce the compromise of weak or stolen credentials.
- Automated User and Group Management
- Change Auditing and Tracking
- Access Reviews and Permissions Auditing
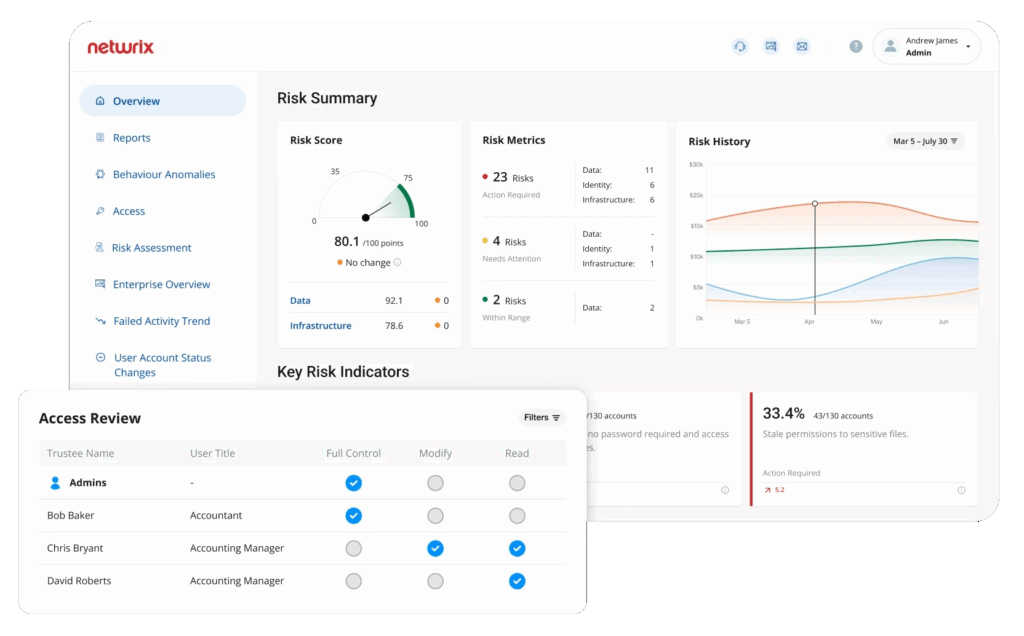
- Data Discovery and Classification
- Data Risk Assessment
- AI-Powered Remediation
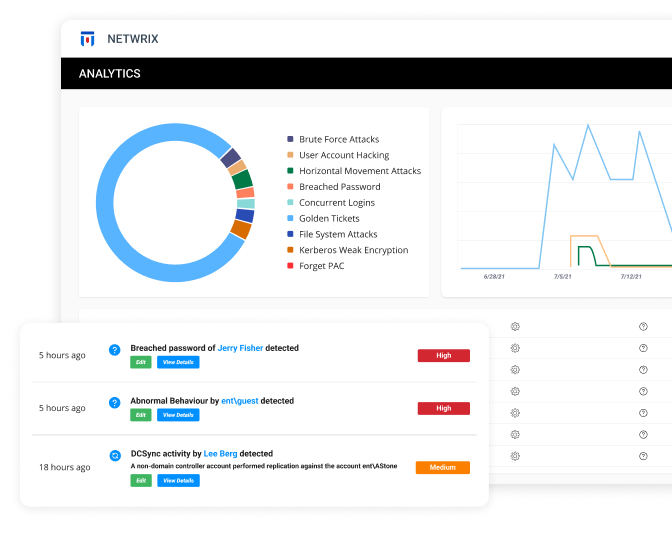
- Threat Detection
- Automated Threat Response
- AD Forest Recovery
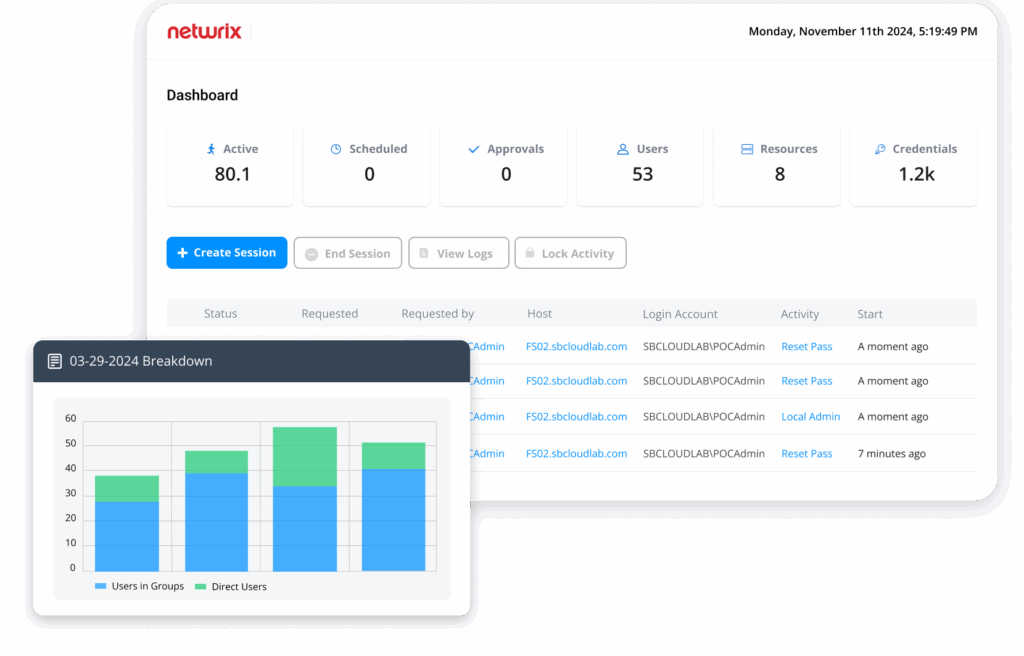
- Zero-Standing Privilege Provisioning
- Session Monitoring and Recording
- VPN-less, Zero Trust Remote Access
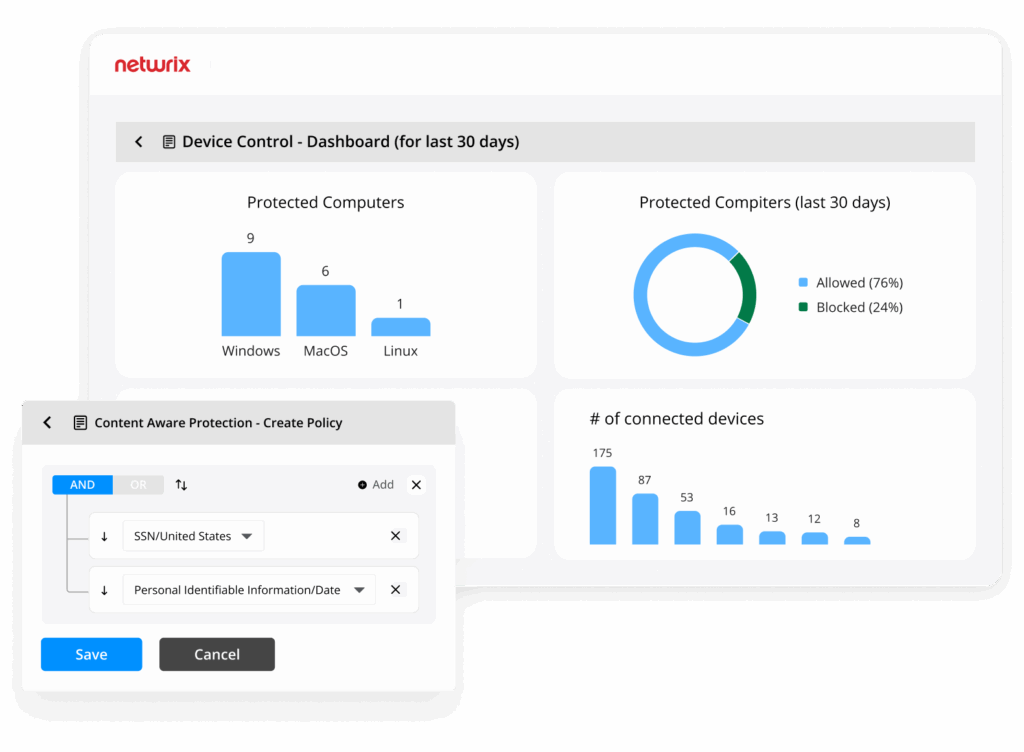
Netwrix provides complete endpoint configuration management, security, and compliance across multi-OS devices and environments. Its policy-based deployment framework prevents attacks and optimizes productivity across the endpoint lifecycle, including privilege
management, peripheral device control, and application security.
- Endpoint Privilege Management
- Device Control and USB Encryption
- Compliance Validation and Monitoring

Get in touch with us:
Bob Stanton – Channel Manager, Netwrix
Bob.Stanton@netwrix.com